The Only Biometric Patient Identification Search to Truly Prevent Duplicate Medical Records and Eliminate Identity Theft
It may not be breaking news that health care facilities are increasingly evaluating the use of biometrics for identifying patients to help prevent duplicate medical records, stop health care fraud at the point of service, increase patient safety, and reduce liabilities. The adoption rate is quickly increasing as more health care organizations realize the potential that biometric patient identification has to achieve these goals plus provide a concrete audit trail of patient activity.
Despite the fact that using biometrics for patient identification is not a brand new concept, there continues to be confusion on how back end biometric searches work and a clear distinction of which searches truly have the ability to prevent a duplicate or overlay from being created and can prevent someone else from assuming your identity.
Let’s review.
We wrote an article last year that appeared in Advance for Health Information Professionals that defines patient identification and patient verification in health care that you may want to review prior to reading the rest of this post.
What you need to know:
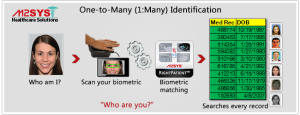
Any type of biometric search that is preceded by a question such as, “What is your date of birth (DOB), name, social security number, eye color, ethnicity, etc.” or any other piece of demographic information is called a one to few (1:Few) search. Essentially what this means is that within the database that the biometric search is executed, the total amount of records are segmented prior to the actual biometric scan and subsequent search. So, instead of you walking into a medical facility and providing only your biometric information (for example, an iris scan) and the search combing through all of the records in the database to identify you, hospital staff are first segmenting the database prior to determining your identity.
Why this is important:
The goal of any biometric patient identification system should be to:
- prevent duplicate medical records and overlays
- increase patient safety
- eliminate health care fraud and medical identity theft at the point of service
- reduce risk
- overcome issues resulting from cultural naming conventions (for example, finding the correct William Jones out of numerous possibilities)
If you rely on a search that requires a qualifying demographic question before scanning your biometric information, the search does not cover all of the medical records in your electronic medical record database, rather it segments the list of names into a much shorter list (for example, all patients with the DOB 01/01/55) before searching for your record. Although this can be partially effective in preventing duplicates and eliminating fraud, it is not a unassailable way to ensure that a patient’s safety is protected by searching the entire medical record database for duplicates, overlays, or fraud. In addition, since you can re-visit the hospital and provide a false birth date after you have already been enrolled and then be enrolled again under the fake profile, is this truly preventing identity theft at the point of service?
Only one to many (1:N) biometric searches have the capability to truly prevent duplicates, overlays, and eliminate identity fraud at the point of service because they are designed to search the entire electronic health record database, not just a segmented list of individuals after asking a qualifying question. 1:Few searches do not search the entire database when performed.
Have you invested in biometric search technology based on 1:Few searches or are you considering an investment? Curious to know more about how searches work, and what types of questions you should ask during the research and due diligence of vendors? Take a look at our Resource Center for detailed information on how biometric searches work and what types of questions you should be asking to biometric patient identification solution vendors.
Remember, if any other piece of information is required from you before executing a biometric search, it is not a true way to prevent duplicates and overlays and eliminate identify theft at the point of service.









