Defining Patient Verification & Identification in Healthcare
Five years ago, it seemed inconceivable that healthcare would be able to use biometrics as a patient identification system. Back then, biometrics was still deeply entrenched in government security deployments, merely grazing the pastures of the commercial marketplace but showing breakthrough potential for practical applications that would begin to spell dividends for a variety of vertical markets. Here we are in 2012 and hospitals all across the world are catching on to the benefits of using biometrics for patient identification; specifically, how it helps:
- raise patient safety standard levels;

Iris biometrics for patient identification uses one to many seaching - reduce hospital liability;
- verify the identity of unconscious patients;
- lower language barriers; and
- prevent medical identity theft.
It is important to note, however, that conspicuously missing from this list of advantages is one of the most essential uses of biometrics for patient identification – the prevention of duplicate medical records.
It is widely known in the healthcare industry that duplicate medical records are a drain on both money and resources as medical facilities struggle to discover a solution that will actively prevent their creation. A biometric patient identification solution can indeed prevent the creation of new duplicate medical records, but only if it is a system based on what is called one-to-many identification (1:N).
As some may or may not know, in biometrics, there are three different ways to recognize a person: verification (one-to-one, or 1:1), segmented identification (one-to-few, or 1:Few) and identification (one-to-many, or 1:N):
Read More: Webinar on Biometric Patient Identification Technology for Patient Safety
One-To-One (1:1) Verification: This method of authentication confirms or denies a person’s claimed identity using a biometric scan and normally follows the physical presentation of an identification document (e.g. social security card, driver’s license, etc.) or the entry of a personal credential (e.g. PIN, username/password). The provided credential locates a stored biometric template that has been linked to it from a prior enrollment. After the credential is provided, the person scans his/her biometric and the captured template is compared against only the stored template that has been located with the credential. Biometric verification (1:1) answers the question, “Are you who you say you are?”
One-To-Few (1:Few) Segmented Identification
This method involves confirming or denying a person’s claimed identity using a biometric scan followed by verbal confirmation to a general identification question (e.g., What is your date of birth?) or the entry of some known general information (gender, race, eye color, etc.). The provided information segments the biometric database so that only a small number of biometric templates are compared against one another following a biometric scan.
Example – A patient walks into the ER and during registration is asked for his date of birth (DOB) before scanning his biometric identifier. If no match is found, then the hospital staff member will create a new medical record and enroll the patient’s biometric template (which will be associated to the medical record). Using another form of ID in addition to the biometric scan drastically reduces the number of biometric templates that are searched. For example, if the hospital has 500,000 stored biometric records and a patient provides a DOB of 10/9/80, only patient biometric templates with this DOB will be searched. Due to this database segmentation, all biometric templates are not compared against during initial enrollment or subsequent visits. This limitation does not prevent duplicate medical records and patient fraud (i.e., a patient could enroll with the same biometric template multiple times).
Infographic: The Cost of Duplicate Medical Records
One-To-Many (1:N) Identification
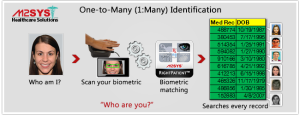
This method of identification determines a person’s identity without any prior claim needed and answers the question, “Who are you?” It substantiates an individual’s identity by comparing a scanned biometric template against all stored biometric templates. A biometric system using the one-to-many approach finds an identity from a database rather than verifying a claimed identity or searching a segmented portion of stored biometric templates.
Example – A patient walks into the ER and during registration is asked to scan her biometric identifier. The captured biometric template is compared against the entire database to see if a medical record already exists. In the absence of database segmentation, the entire medical record database is scanned to ensure a duplicate medical record is not created for this patient to prevent the chance of fraud.
Biometric patient identification systems based on 1:1 or 1:Few matching require medical facilities to ask patients for some form of identification or credential before the patient performs a biometric scan. The identification or credential provided (e.g., DOB) locates a specific patient record or group of records (e.g., list of patients with a specific DOB). When a biometric scan is performed, the captured template is only compared against one record (verification) or a very small, segmented group of records (1:Few). This does not provide a mechanism to compare the patient’s scanned biometric template against all records in the database to check for duplication or to prevent someone from being registered under multiple IDs. 1:1 and 1:Few verification will not prevent a duplicate record from being created and opens the door for patients to enroll under multiple identities and commit fraud.
In contrast, 1:N searches will scan the entire master patient index each time a patient attempts a biometric enrollment (de-duplication) and each time he or she checks in anywhere within that healthcare network (provided the patient registry is shared across the system). Providing the sole means of preventing duplicate medical records by searching each patient’s template in the entire system instead of only those who are grouped in a list after presenting an initial form of ID, 1:N searches are the only true way for healthcare to raise the level of patient safety, lower liability risks, and strengthen medical identity theft prevention programs.
Due diligence is very important before investing in a biometric patient identification system. Is your organization asking the right questions before piloting or purchasing a solution?
A version of this first appeared on Advance for Healthcare Information Professionals.









